What are DoS / DDoS attacks?
DoS (Denial of Service) Attacks
The common Dos attack is where hackers use a relatively powerful single computer to attack a target IP, this is a one-to-one attack (DDoS is a many-to-one attack). DoS sends a large number of meaningless network messages to the target IP in the form of message flooding, exhausting system or network resources and making the service unable to operate normally.
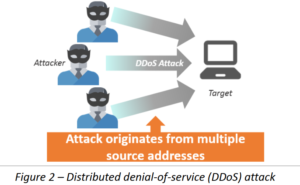
DDoS (Distributed Denial of Service) Attacks
DDoS has evolved from DoS. DDoS attacks allow hackers to take control of multiple malwareinfected computers or other devices such as IoT devices, this is becoming what is often heard as a “zombie computer”. As the source of attack traffic, these zombie computers launch a “denial of service” attack on a specific target IP, introducing a large amount of network traffic, overwhelming the server or network, causing the host to temporarily interrupt or stop the service.
Lantech solutions to prevent DoS / DDoS attacks
Lantech OS3/OS4 switches adjust the access rules, strengthening the screening mechanism, limits and blocks abnormal IP addresses or abnormal request packets, this reduces the possibility of a large amount of invalid data occupying bandwidth or consuming resources, this then achieves the effect of blocking DoS/DDoS attacks.
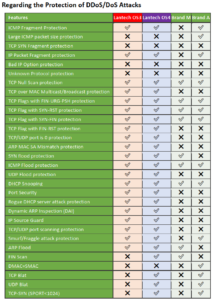
Lantech OS3/OS4 Switches’ Mechanisms for DoS/DDoS Attacks
Lantech OS3/OS4 Switches’ Mechanisms for Suspicious Packets DoS/DDoS Attacks
- ICMP Fragment Protection
- IP Packet Fragment Protection
- TCP Null Scan Protection
- TCP over MAC Multicast / Broadcast Protection
- TCP Flags with FIN-URG-PSH Protection
- TCP Flags with SYN-RST Protection
- TCP Flags with SYN-FIN Protection
- TCP Flags with FIN-RST Protection
- TCP/UDP port is zero Protection
- ARP MAC SA Mismatch Protection
- FIN Scan (OS4)
Lantech OS3/OS4 Switches’ Mechanisms for Network DoS/DDoS Attacks
- SYN Flood Protection
- ICMP Flood Protection
- UDP Flood Protection
- DHCP Snooping
- Port Security
- Rogue DHCP Server Attack Protection
- Dynamic ARP Inspection (DAI)
- IP Source Guard
- TCP/UDP Port Scanning Protection
- Smurf/Fraggle Attack Protection
- ARP Flood
- TCP Blat (OS4)
- UDP Blat (OS4)
- TCP-SYN (SPORT<1024) (OS4)
Conclusion
The reason why DDoS defense is difficult is that DDoS “attacks” will be packaged with seemingly normal “needs”, and the source of the attack is also difficult to trace. However, the following four aspects can still be used to strengthen the system’s DDoS defense:
- Implement periodic information security testing.
- Regular adjustments of the rules of the road for protective equipment
- Improve the equipment performance and specifications of the service system
- Adopt mechanisms with DDoS defense or DDoS mitigation
Using Lantech OS3/OS4 switches with DDoS attack protection mechanisms can not only protect the switch itself, but also protect the backend devices connected to the switch, such as servers, cameras, and wireless APs.



 Lantech is dedicated to providing the best quality and service to our customers. We proudly provide 5 years warranty to our industrial products.
Lantech is dedicated to providing the best quality and service to our customers. We proudly provide 5 years warranty to our industrial products. 
